 Today the new week started, so there has to be a new article in my “Best of Web” series. Although I reached my selfmade aim (to post an Best of Web article on every monday) again this week, it is, jast as the last few times also, late in the evening. So maybe I should better announce my series as follows: “Best of the Web is a weekly series of articles, which will be, if at all, published in the night from Monday to Tuesday.” Anyway – Monday is Monday and so it goes to the next round.
Today the new week started, so there has to be a new article in my “Best of Web” series. Although I reached my selfmade aim (to post an Best of Web article on every monday) again this week, it is, jast as the last few times also, late in the evening. So maybe I should better announce my series as follows: “Best of the Web is a weekly series of articles, which will be, if at all, published in the night from Monday to Tuesday.” Anyway – Monday is Monday and so it goes to the next round.
This week the topics are very software-heavy – which exactly means that all articles, except for two in which the hardware is mentioned, will deal with software and software problems this week. The spectrum ranges from operating systems via web programming in PHP to C# code optimizations.
Before presenting the links of the week, I would like to take this opportunity to once again point out that I gladly accept link recommendations anytime. So if you know a readable website, then let know about it. If the quality of the text/content is good enough, you may also like to submit links to your own site – crucial for a nomination in the Best of the Web Round-up is whether I like the article and I think it gives a value for the majority of my readers. If an article filfils this criteria, it doesn’t matter if it’s a link to your or someone else’ site.
How to get shell access on any Android device
Actually, one might think that the data on your own smartphone is protected against the coarsest when the smartphone is locked and provided with a security code. But that’s not 100% correct. An attacker could grab the smartphone and attain (shell) access to the device via USB and ADB without knowing the security code. So if you leave your phone in office while making a new coffee an attacker could get access to your data. Since this is obviously a security risk, you can disable the ADB shell access. Now one might think that the device then (with diabled ADB) is safe against this kind attack. But this is also a misjudgement. At this year’s Toorcon (a hacker conference in San Diego) Michael Ossmann and Kyle Osborn presented a means by which it is possible to obtain (despite disabled ADB Shell) shell access on any Android device. For this purpose they use the fifth pin of the USB Micro connector which was originally implemented to distiguish between different USB connector. If you want to know how their proof of concept looks like, your can read this article or watch their complete session at the Toorcon as video.
A cryptoraohically secure rand()-function in PHP
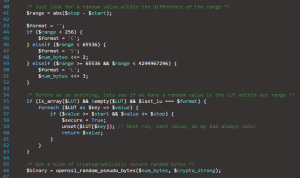 There are quite a few discussions, threads and articles about PHP’S rand() function and its reliability on the internet. So I have also written an article about the rand()-function and its reliability. Nikolai has picked up the whole story again and wrote a cryptographically secure implementation of a pseudo-random number generator. The footprint of his function is similar to the footprint of the classic rand()-function, so that it should possible to replace the classic rand() with Nikolai’s function without major effort. The article on Nikolai’s blog encloses the implementation of his cryptographically secure random generator and goes further into the technical details.
There are quite a few discussions, threads and articles about PHP’S rand() function and its reliability on the internet. So I have also written an article about the rand()-function and its reliability. Nikolai has picked up the whole story again and wrote a cryptographically secure implementation of a pseudo-random number generator. The footprint of his function is similar to the footprint of the classic rand()-function, so that it should possible to replace the classic rand() with Nikolai’s function without major effort. The article on Nikolai’s blog encloses the implementation of his cryptographically secure random generator and goes further into the technical details.
LockBits in C# – image processing on a new level
Anyone who has ever ventured to the processing of image files in C#, certainly got in touch with the SetPixel() – and the GetPixel()-function of the Bitmap class. Most times these two are the first functions encountered when one deals with the manipulation of images using the .NET framework. But who wants to change more than just 1 or 2 specific pixels in an image, will have certainly noticed that the whole thing is really computation intensive and slow. And that’s where LockBits comes into play. It’s another method to process images and that up to 100x faster because LockBits works directly on the raw image data. So who has not heard of LockBits until now and occasionally works with images in C# or another .NET language, should definitely read Bob’s article on Lockbits.
20 WordPress plugin tutorials
 I’m sure that one or the other reader of my blog is a webmaster. And I dare to say that even one or the other among you is a blogger who has WordPress in use. For those of you the following link tip could be really interesting. Although the variety of WordPress plugins is almost inexhaustible, there is always and everytime one or the other case, where you just can’t find the WordPress plugin which fits your needs in a 100% way. Or perhaps you even have ideas yourself for a plugin which does not yet exist it that way. The following link list contains 20 tutorials about WordPress plugins and how to build them. I think it’s a good starting point to program your first own and selfmade WordPress plugin.
I’m sure that one or the other reader of my blog is a webmaster. And I dare to say that even one or the other among you is a blogger who has WordPress in use. For those of you the following link tip could be really interesting. Although the variety of WordPress plugins is almost inexhaustible, there is always and everytime one or the other case, where you just can’t find the WordPress plugin which fits your needs in a 100% way. Or perhaps you even have ideas yourself for a plugin which does not yet exist it that way. The following link list contains 20 tutorials about WordPress plugins and how to build them. I think it’s a good starting point to program your first own and selfmade WordPress plugin.
Windows on the Raspberry Pi
The last link in this week’s round up deals again with the Raspberry Pi. And also, if this is indeed a piece of hardware, again it is all about the software. More specifically, it is about a project by a few resourceful people from the official Raspberry Pi Forum who have started to port Windows to the Raspberry Pi platform. To keep your elation at bay, I have to say at this point that they port Windows CE and not a regular Windows x86 or Windows x64. So Windows CE, which means “Compact Edition”, is only able to execute programs specially compiled for Windows CE. But if you come out of the industry and had ever to do with Windows CE, you nevertheless might observe this development with courtesy. The number of “homebrew platforms” which are supporting Windows CE is indeed not too large. When the whole thing comes in a more advanced stage, I will certainly try and see if I’m able to run one or the other application on the Raspberry Pi using the .NET Compact Framework. Everything else can be found here: Windows on the Raspberry Pi.
Short film: The life of a teenager in 17 minutes
The subsequent, 17-minute long, short film titled “Noah” was presented at this year’s Toronto International Film Festival. The special thing about the film is that it completely takes place on screen of a teenagers Mac. This means that the while film is like a 17-minute screencasts. At first sight this may sound not be as spectacular, but hindsight is highly recommended. So if you can spend a quarter of an hour for a really good movie, you should run the following short film once to your mind. To watch the movie, simply click on the thumbnail below!


Nice blog! I really like your information.
Wow it’s wonderful. Keep update with new blogs.
WOW!!! Just found your blog. THIS IS AMAZING!!!!
gothic shirts