After we set up an OpenSSH server in the first part and completed the basic configuration to secure the server in the second part of this article series, we now want to configure the server to make use of a key file (hereinafter also “key”) for the login process.
The SSH key authentication is based on the principle of asymmetric encryption. So we need a key pair consisting of a public key and private key. The public key is then stored on the OpenSSH server and the private key goes to the client.
The top priority here is to keep the private key secret forever and in any case. If someone else comes into the possession of the private key, he or she can log on to your server.
As a small obstacle you can provide the private key itself with a password. But nevertheless, if the private key gets public or falls into wrong hands, it should quickly be ensured that the counterpart, the corresponding public key, is removed from the OpenSSH server.
To generate a key pair, there are several possibilities. Two of them I will explain further below. One possibility is the creation by means of the command line tool “ssh-keygen”. This comes with the installation of OpenSSH and is therefore available atleast for Linux. The OpenSSH for Windows package hadn’t included ssh-keygen at the time, when I wrote this article.
If you prefer working with a graphical interface, you should have a look at the second option presented. By using the program “PuTTYGen” you can create the required key pair without getting in touch with the commandline. Furthermore PuTTYGen is also available for Windows.
How to generate a key pair using ssh-keygen
One way to generate a key pair is using ssh-keygen. However, this tool is not included in the OpenSSH for Windows installation. Either you need access to a Linux machine or you use the Linux server, which runs your OpenSSH server.
Note: You should only use your OpenSSH server Linux machine if you are really sure that no one unknown has access to this server. This would be the case, for example, if your machine is a media server on your LAN where you know and trust all the network users and the server does not have internet access. Especially in shared server environments, you should exercise with highly raised caution or better generate the key on a local machine.
To generate a new key pair with ssh-keygen, you need the following command.
ssh-keygen -t rsa -b 4096
The -t parameter here specifies the encryption method. (For SSH version 2 you should use RSA, as in the example, but DSA would also be a valid choice.) The -b parameter specifies the key length in bits.
During the execution of the command you will be prompted for a password. Here it is important to find a good compromise between complexity and the effort for the respective input of the password. (A longer and more cryptic password may be more secure, but it’s also harder to type. And you’ll have to type it at every login!)
Important: Although there is also the option to enter no password, but it is strongly discouraged. If you set up no password, so an attacker, as described in the introduction of this article, is sufficient to log on your server with only the key! If you assign a password, the attacker needs to break this before he can login. This in turn should give you time frame which is big enough to remove the corrupted public key from your server and exchange it with a new one, before the attacker can crack your passphrase/private key.
After generating the key pair, you should have two files now.
id_rsa id_rsa.pub
The file with the .pub extension is your public key and deserves on the server. If not exists, create a folder called “.ssh” in your home directory and copy the public key file into this folder.
sudo mkdir -p ~/.ssh sudo mv id_rsa.pub ~/.ssh
Finally, you have to add your public key to a file called “authorized_keys”. You can do this with the following command.
cd ~/.ssh sudo cat id_rsa.pub >> authorized_keys
Hwo to generate a key pair using PuTTYGen
Those without access to a local Linux computer and those who don’t want to generate the key pair server-side, can for example use PuTTYGen. This is the key generator of the famous PuTTY suite. PuTTYGen you can be download free. PuTTYGen is portable, so installation isn’t needed.
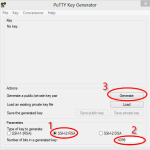 After the start you can choose the length of the key in bits and the encryption method. After that, you have to click on “Generate” to start the key generation. To accelerate the generation, you can drive around randomly with your mouse on the surface of PuTTYGen. The movements are used as random data and included in the calculation process of the key.
After the start you can choose the length of the key in bits and the encryption method. After that, you have to click on “Generate” to start the key generation. To accelerate the generation, you can drive around randomly with your mouse on the surface of PuTTYGen. The movements are used as random data and included in the calculation process of the key.
If the key is created, you should still create a password for the private key. This protects the key in case of theft as I said. (At least for a time.) Just write the password in the fields “Key passphrase” and “Confirm passphrase” which are visible after the generation of the key.
After setting the password, private and public key can be exported using the two “Save”-buttons. The public key must now be transferred to your OpenSSH server (for example by using a USB stick, SSH/SCP, FTP, etc.).
Once arrived on the server, the key must be written to a file called “authorized_keys”, which should be located in the folder “~/.ssh”. (If that’s your first key, you may have to create the “.ssh” folder.)
sudo mkdir -p ~/.ssh sudo mv id_rsa.pub ~/.ssh
Then add the public key to the “authorized_keys” file.
cd ~/.ssh sudo cat id_rsa.pub >> authorized_keys
Set up the key in your OpenSSH server configuration
In the last step, the configuration file of the OpenSSH server still needs to be adjusted, so that it allows login via key file and forbid login by plain password. Therefore open the sshd_config.
sudo vim /etc/ssh/sshd_config
And change the line that starts with “PasswordAuthentication”, as follows.
PasswordAuthentication no
With this setting, the login by password will be forbidden and so only users with key files can login. Thus, all brute force and password list attacks will be useless.
To apply the changes you have to save and close the sshd_config and then reload the changed settings in the OpenSSH service once. This goes as follows.
sudo service ssh reload
Now the server-side configuration part is complete. In the next paragraphs I’ll show you how to login with OpenSSH console client and PuTTY by use of the private key.
How to logon using OpenSSH and private key
The login with a private key works with both OpenSSH and with OpenSSH for Windows. The required command is almost identical to what I showed you in the first part of the article series. There is still only one additional parameter. The “-i” parameter.
ssh myusername@myip -p myport -i "PathToMyKey"
“myusername” is the name of the account on the SSH server with which you want to sign in.
“myip” can either be the IP address of the server or, alternatively, its host name.
“-p myport” is optional and should be specified if you have changed the port, your SSH server is running on.
“”PathToMyKey”” must be specified depending on the operating system you use. On Windows with backslashes and on Linux with slashes. Examples: Windows => “C:\mykeys\id_rsa”. Linux => “~/mykeys/id_rsa”.
How to logon using PuTTY and private key
To log on using Putty and your own private key, the private key must be specified in the settings of PuTTY. This can be done in the menu item “Connection=>SSH=>Auth”. However Putty needs the key to be in its own PPK format. If your private key has been generated with ssh-keygen you have to convert it first. (If you have already done this you can skip the next paragraph.)
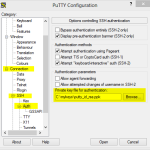 To convert the private key in to the PPK format, we need again the “PuTTYGen” tool. Start it and click on the “Conversions=>Import key” menu item. Then choose your private key file and open it. Using the button “Save private key” you can then save you private key file in PPK format.
To convert the private key in to the PPK format, we need again the “PuTTYGen” tool. Start it and click on the “Conversions=>Import key” menu item. Then choose your private key file and open it. Using the button “Save private key” you can then save you private key file in PPK format.
If you now have your private key available in PPK format, open PuTTY. In PuTTY load your connection settings or set up some new connection settings. Before you connect to your server, enter the menu and navigate to “Connection->SSH->Auth”. Here you can find a field named “Private key file for authentication:”. Enter the path to your private key in this field. That’s it. When you connect to your server via PuTTY it is using the preset key file for login authentification.
Conclusion
Thus, we were at the end of the three-part article series. I hope you learned maybe the one or other thing. If you still have questions or suggestions for another article, then let me know it in the comments.



